How to Override Default Authentication Handling
SIP provides a feature to the SIP client to handle authentication handling for services such as registration and session establishment. By default, this authentication challenge handling is handled by the SIP server using the digest mechanism. This mechanism is used by profile plug-ins that implement nondefault SIP behaviour which is also known as extensible Service Provider (xSP).
These components are used when a SIP client handles authentication challenges independently. When an authentication problem is reported use CSIPAuthorizationHeader and CSIPProxyAuthorizationHeader objects to manipulate the registration or session initiation request headers. Then re-register a profile or reinitiate a session using the updated headers.
To enable a client to override default authentication handling mechanisms, it must inform the SIP server by disabling the built-in security mechanism of the SIP using the CSIP::SetSecurityHandlingL() function. The client uses CSIP::IsSecurityHandlingEnabled() function to determine what is handling the authentication challenges. This function returns ETrue if the built-in security mechanism of the SIP is used.
When a SIP client handles authentication challenges independently, it uses CSIPAuthorizationHeader and CSIPProxyAuthorizationHeader objects to manipulate the registration or session initiation request headers when an authentication problem is reported. Re-registration of a profile or reinitiating a session is done using the updated headers.
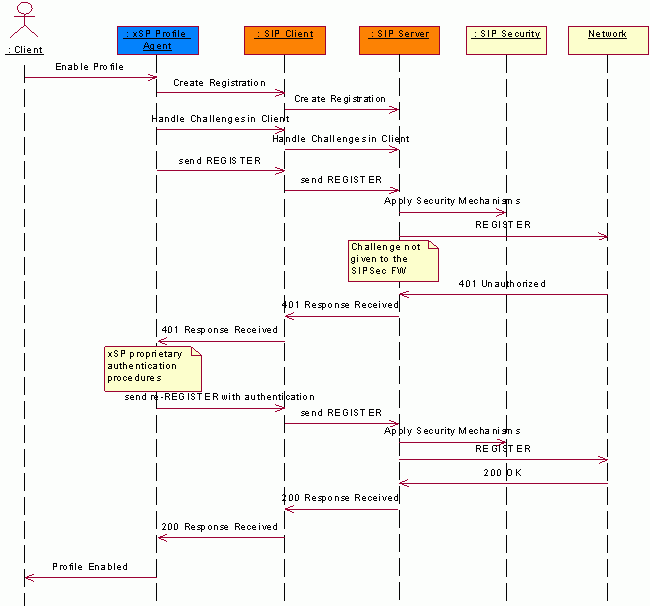
In the following illustration the client handles authentication challenges related to the profile registration. All authentication errors are then forwarded to the xSP profile agent plug-in. When an error is reported to the plug-in, it runs a proprietary authentication procedure and tries to re-register the profile.
The following illustration shows the call flow of handling authentication challenges while registering a SIP profile:
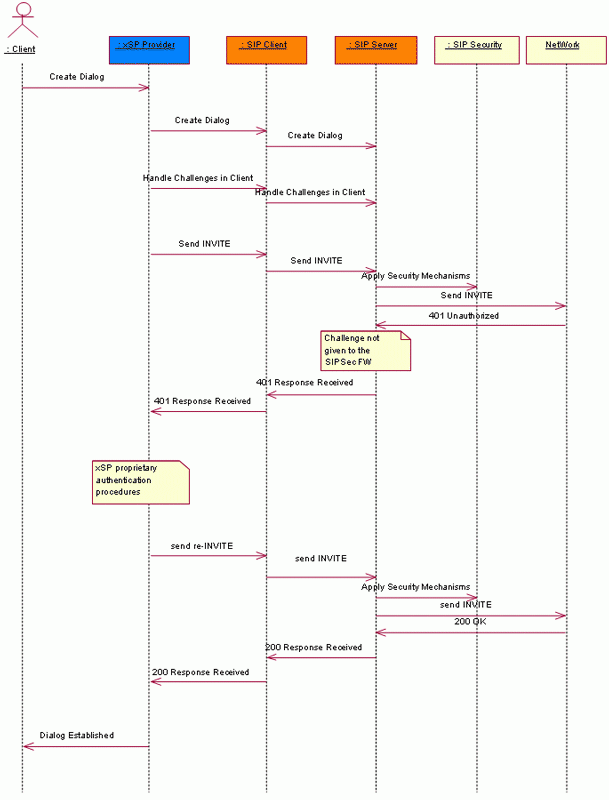
In the following illustration the client handles authentication challenges related to the session initiation. All the authentication errors are then forwarded to the xSP provider. When an error is reported to the provider, it runs a proprietary authentication procedure and tries to reinitiate the session.
The following illustration shows the call flow of handling authentication challenges while establishing a session: