ASN-PKCS Overview
The ASN-PKCS component provides interfaces for:
Performing ASN.1 -DER (Abstract Syntax Notation One - Distinguished Encoding Rules) encoding and decoding of PKCS (Public-Key Cryptography Standards) private keys in raw text as well as PBE (Password-Based Encryption) encrypted forms.
Performing ASN.1 encoding and decoding of PBE parameters associated with the private keys.
Key concepts and terms
- Key
A cryptography key is a constant value applied using a cryptographic algorithm to encrypt text or to decrypt encrypted text.
Keys are classified as symmetric and asymmetric based on the type of algorithm applied. If the same key is used for both encryption and decryption, it is symmetric. If different keys are used for encryption and decryption, they are asymmetric. Asymmetric keys exist in the form of a public and private key pair, where the public key is used for encryption and the private key is used for decryption.
- Key Store
A key store is a repository of keys that can be retrieved and used to accomplish a variety of tasks.
The key store provides the following functionality:
Architecture
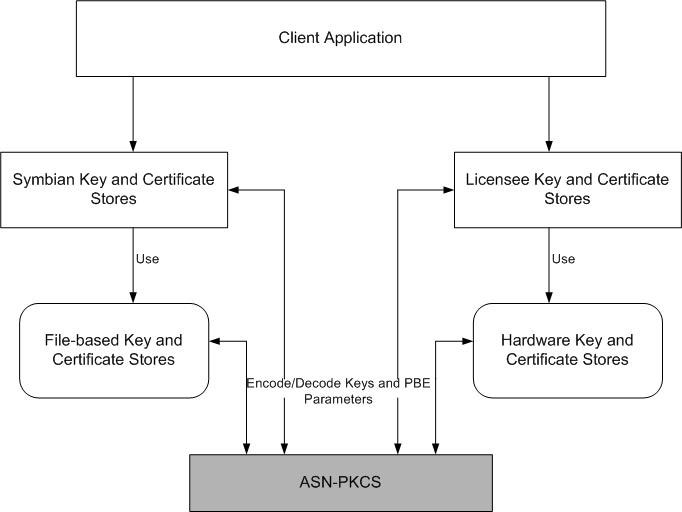
The following block diagram describes the interaction of the ASN-PKCS component with the certificate and key stores:
The client application accesses the various certificates and keys of the device stored in the respective stores. Depending on the requests received from the store management and implementation components, ASN-PKCS acts on the keys during certain key and certificate manipulation operations. For details of the operations during which the ASN-PKCS APIs are invoked, see Typical uses.
APIs
| API | Description |
|---|---|
Provides the means to decode PKCS#8 encoded private keys. |
Typical uses
ASN-PKCS APIs are used for encoding and decoding purposes during the following key and certificate manipulation operations:
Encoding and decoding of PKCS private keys (in raw text and PBE-encrypted forms) during import and export of keys. When PBE-encrypted PKCS keys are imported or exported, the ASN-PKCS APIs also help in encoding or decoding of the PBE parameters.
Encoding of the private keys accompanying public key certificates (according to PKCS#12 standards) while creating certificate requests.
Creation of PKCS#7 messages for creating the certificate requests.
Notes:
Device creators can use the ASN-PKCS component along with their own implementation of the certificate and key stores.
For details of the key and certificate operations, see Unified Keystore Tutorials and Unified Certificate Store Tutorial respectively.